The data held by the healthcare industry is highly confidential and includes details on every birth and death, every immunization, basically every interaction you’ve ever had with a medical professional.
As a key target for hackers and state sponsored cyber-thieves it is thought that the value of a healthcare record is seven to ten times greater than a credit card record. This is because protected health information (PHI) has a longer “shelf life” than traditional financial data, and it can provide a unique view to a population for foreign governments.
When hackers succeeded in stealing, or even deleting thousands of medical records, the resultscan be catastrophic. Not only does it damage the organizations reputation and potentially result in numerous lawsuits, there are clearly negative implications for the rights of patients and customers.
IT professionals are fighting to secure information, appropriate access and confidentiality — all within an environment where immediate access to data is literally life and death.
Start with the basics – training and procedures
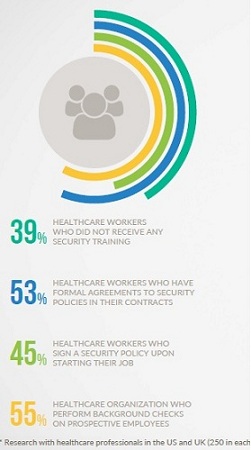 But where should healthcare organizations direct their focus not only help to safeguard sensitive patient data, but also to satisfy an array of overlapping compliance requirements from the Health Insurance Portability and Accountability Act, or HIPAA to the United Kingdom’s Data Protection Act.
But where should healthcare organizations direct their focus not only help to safeguard sensitive patient data, but also to satisfy an array of overlapping compliance requirements from the Health Insurance Portability and Accountability Act, or HIPAA to the United Kingdom’s Data Protection Act.
First, address the human aspects of security by providing effective ongoing training and ensuring you have robust security procedures in place. Make sure you create and share a security policy with everyone in your company and include any penalties for poor security that will be enforced.
Our research however showed that across healthcare, 39% of employees did not receive IT training upon joining the company and 37% of companies did not even have a documented IT security policy to speak of. These naïve and irresponsible approaches to securing sensitive data speak volumes about how easy it is for hackers to access a healthcare network.
It’s thought that 70% of the data losses are caused by human error so these negligent users are your unwitting participants in phishing and social engineering scams. They take the bait and help to infect endpoints with malware that may be the attack (as in the case of ransomware) or simply provide a foothold for further actions by criminal online organizations.
Users are human. Training will never be enough
But creating a culture of safe IT practices amongst everyone in your company is not enough. Users are human, they are flawed, and they are careless and often exploited. They will always act outside the boundaries of policy and sometimes common sense. Whilst most individuals given the appropriate information, will pursue a course of action that supports the organization’s security initiatives, most is not all. This trust needs to be verified. An organization cannot continue to blame the user and demand even more training.
What’s more, it isn’t always an incompetent or ill-prepared member of staff who opens up a company’s data to hackers.
The Malicious Insider or External Attack
Malicious users are your insiders that have shifted their loyalty from the organizationwhere they work to themselves, and are engaged in some kind of inappropriate activity (such as hacking, data theft, etc.) that benefits themselves over the organization.
The external attack is likely more a member of an organization than a loner. These individuals leverage hacking, social, malware, and many other toolsets to create a way into your network. Once inside, they work to take on one or more sets of elevated credentials to provide them with greater access and an ability to move about the network in an attempt to identify valuable data.
Spotting any of these is difficult.
When you boil it down, the only way to really tell if someone has been exploited, is a malicious insider or an intent external threat actor is by allowing them to perform actions (such as launching applications, authenticating to systems, accessing data, etc.) and determine whether the actions are inappropriate.
But given the majority of your user population doesn’t act the same way each day – let alone the next week or month – it makes more sense to spot the threat actor by looking at leading indicators of threat activity, rather than waiting for the threat activity itself.
One of the most accurate leading indicators is one no malicious insider or external threat actor can get around – the logon.
Stopping threats at the logon
The simplest and most common activity to every threat action is the logon. Nearly all threat actions require a logon using internal credentials. Endpoint access, lateral movement between endpoints, external access via VPN, remote desktop access, and more all share the common requirement of a logon.
The concept of logon management centers around four primary functions – all working in concert to maintain a secure environment:
- Policy & Restrictions – Establishes who can logon when, from where, for how long, how often, and how frequent (simultaneous sessions). It can also limit specific logon types (such as console- and RDP-based logons).
- Real Time Monitoring & Reporting – Every logon is monitored and tested against existing policies to determine if a logon should be allowed. Reporting helps ensure detailed insights for any investigations.
- IT and End-User Alerting – Notifies IT and the user themselves of inappropriate logon activity and failed attempts.
- Immediate Response – Allows IT to interact with a suspect session, to lock the console, log off the user, or even block them from further logons.
In essence, logon management makes the logon itself a scrutinized and protected event.The ability to successfully logon (and remain logged on) becomes more than just whether the right credentials are used.
A logon management solution will detect an abnormal access attempt based on the customized and granular logon policies that are set for that particular account (employee). It will act accordingly – either denying or approving the logon – and alert IT (or the appropriate user themselves) if stipulated.
No logon, no threat
Logon Management is a simple, efficient and effective means of thwarting potential threats. It provides a protective layer at the logon, which logically exists before action occurs, to stop the threat entirely. No logon, no threat.
 Some of the potential insider threat scenarios that are now thwarted include:
Some of the potential insider threat scenarios that are now thwarted include:
- Genuine but compromised logins from exploited users are now useless to malicious insiders or would-be attackers.
- Careless user behavior such as password sharing, shared workstations left unlocked or logging into multiple computers simultaneously is now eradicated.
- Access to any data/resource is now always identifiable and attributed to one individual user. This accountability discourages an insider from acting maliciously and makes all users more careful with their actions.
- Suspicious activity is alerted on offering IT the chance to instantly react.
- Users are notified with tailor-made message and alerts – including alerts on their own trusted access. Informed employees are another line of defense.
For Windows-based networks, IS Decisions logon management solution, UserLock, provides a comprehensive layer of security at logon. Using a mixture of enforceable logon policies, alerting, and response actions, UserLock uniquely empowers IT organizations to leverage the active directory logon as a critical security checkpoint – before threat actions take place.
No technology can completely eliminate the chance of an attack, but there is a way to drastically reduce the potential risks. Tools such as UserLock offer greater control for admins and completely restrict various careless user behaviors, as well as encouraging good behavior through alerts and notifications. Just what the doctor ordered.






















